If you use AzireVPN or PIA with OpenVPN you can tunnel all your traffic via VPN tunnel in order to hide from Geoblocking or censorship.
To use this also with OPNsense here a short guide how to set up a server and client with OPNsense. Configuration for e.g. Android should be quite the same.
Server
Since the plugin is still in development install via Console:
# opnsense-code plugins
# cd /usr/plugins/net/wireguard
# make upgrade
After this you have it under VPN – WireGuard and do the following like in the screenshots below
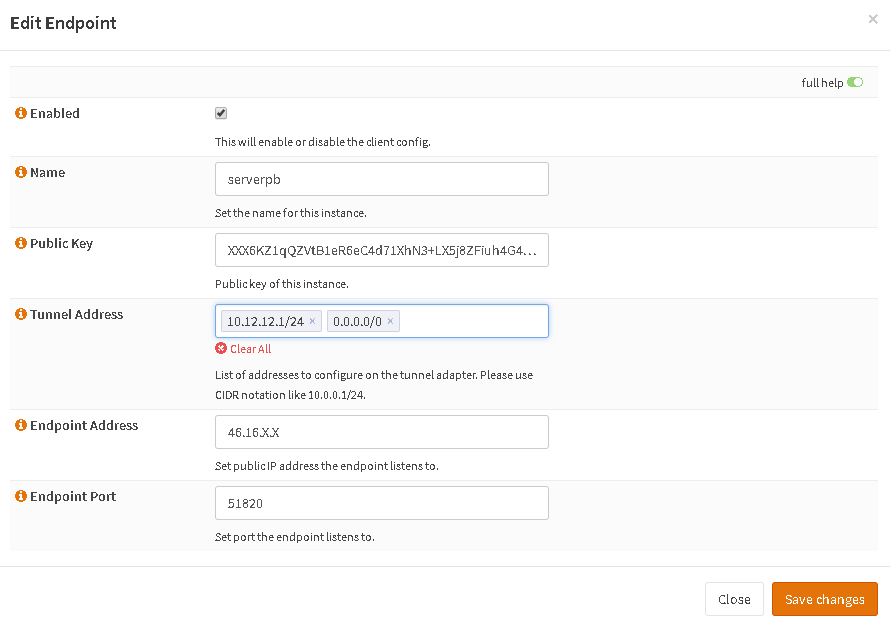
This is the Endpoint, so your client. Insert the pubkey and give it a Tunnel Address, I used 10.12.12.2/24. Endpoint address can be empty, so any address is allowed.
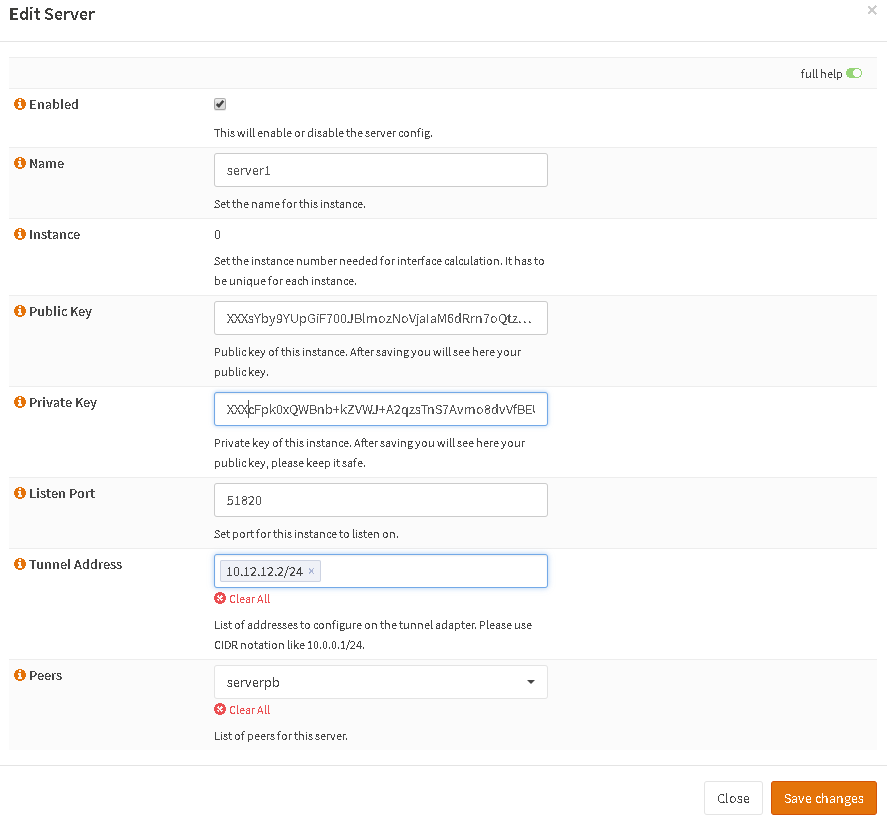
Create a new server instance, give it Tunnel Address 10.12.12.1/24 and link your newly created Peer.
Enable the service and go to Firewall – Rules to add a new Firewall rule. If you don’t see tab WireGuard just edit an existing rule, change nothing and save again. Then you should see the tab.
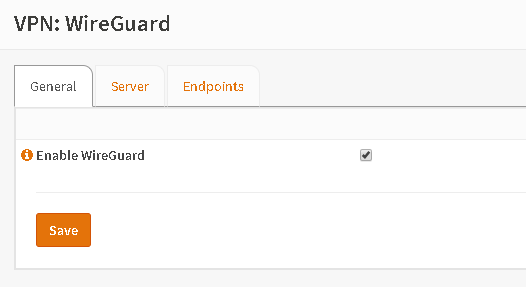
For testing just allow everything.
Now go to Firewall – NAT – Outbound and add a new rules, interface WAN and set as source your Tunnel Network 10.12.12.0/24
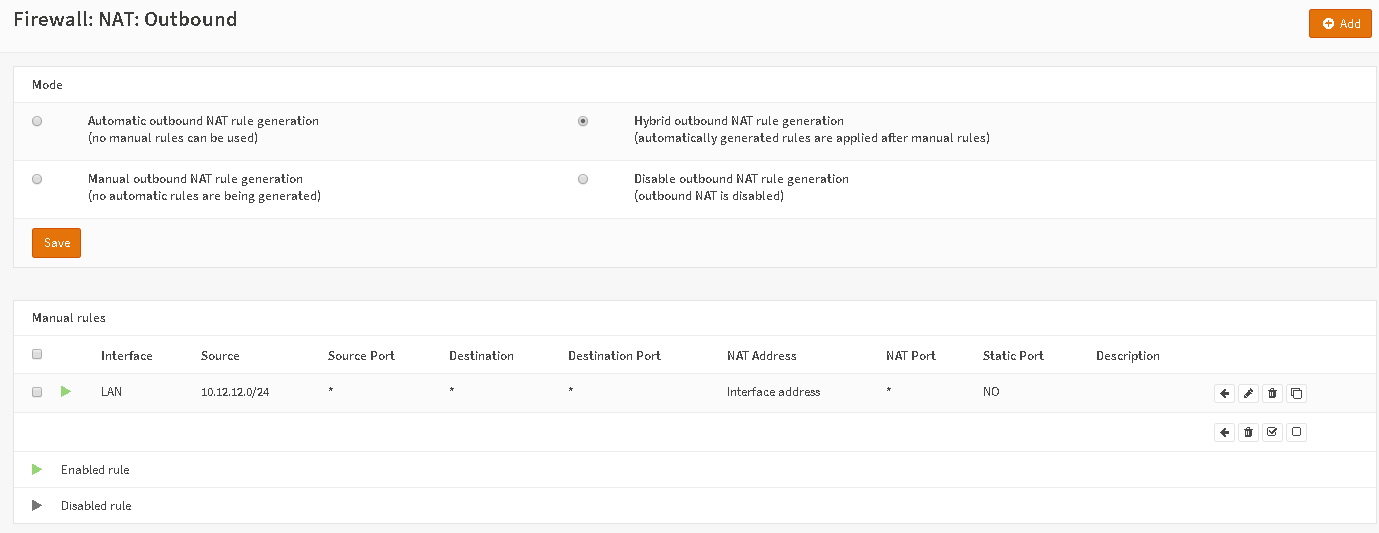
This would mean that packets from 10.12.12.0/24 leaving WAN are natted.
In my case it’s LAN since this central OPNsense only has one interface.
Client
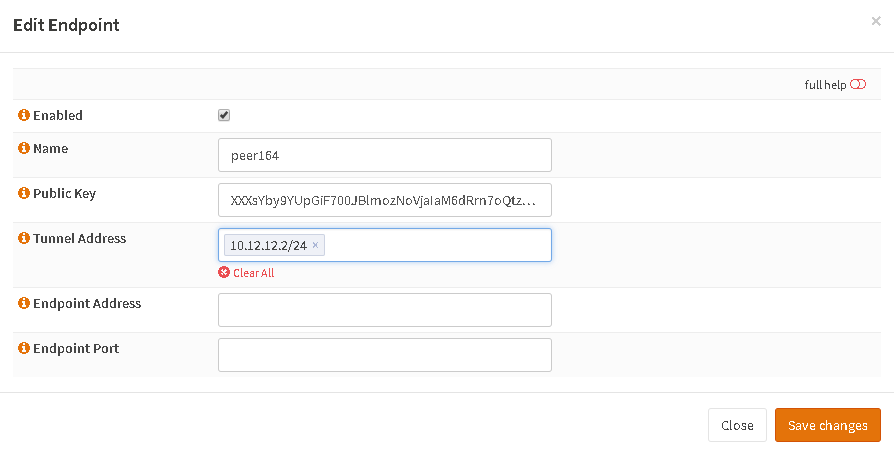
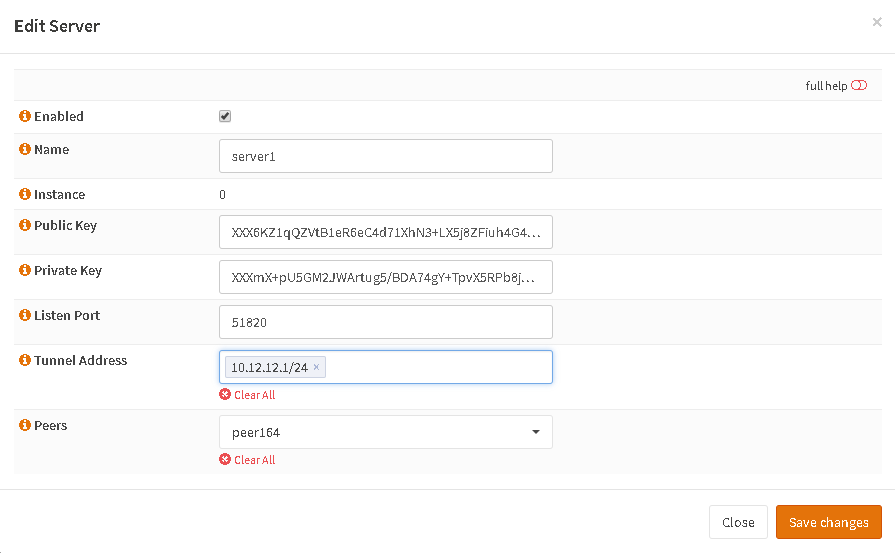
On the client install the pkg same as above and again go to WireGuard, create Endpoint with pubkey from server, create a server instance and link the endpoint, enable and you are good. Packets are pushed via VPN. In the screenshots look at the values, they are a bit different that in server since we add 0.0.0.0/0