This guide explaines how to easily roll out client certificates, i.e. for mobile phones to use certificate based authentication for Exchange or EAP-TLS.
It assumes you have followed this guide and use these versions:
http://www.routerperformance.net/howtos/install-privacyidea-2-13-on-a-clean-debian-8-jessie/
I’ll insert a compatibility table after some new versions.
Create a new CA for privacyIDEA (please note, you have to set a PW for the root key, but currently it’s required to delete it afterwards):
- mkdir /etc/privacyidea/CA
- cp /opt/privacyidea/lib/python2.7/site-packages/tests/testdata/ca/openssl.cnf /etc/privacyidea/CA/
- openssl req -days 3650 -new -x509 -keyout /etc/privacyidea/CA/ca.key \
-out /etc/privacyidea/CA/ca.crt \
-config /etc/privacyidea/CA/openssl.cnf - touch /etc/privacyidea/CA/index.txt
- echo 01 > /etc/privacyidea/CA/serial
- openssl rsa -in ca.key -out ca-nopw.key
- mv ca-nopw.key ca.key
- chown -R privacyidea /etc/privacyidea/CA
- chmod 0600 /etc/privacyidea/CA/ca.key
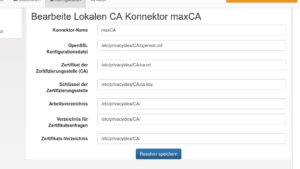
Now you configure a new CA connector via PI (sorry, it’s in German):
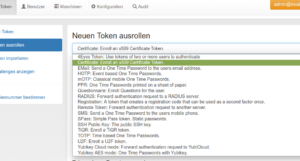
As an admin enroll a certificate token to a user:
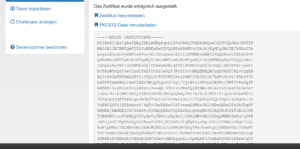
And you are done:
Attention:
With PI 2.13 it’s important, when you have set a PIN at the enrollment (which is the import pw), do NOT download the pkcs12 directly after the creation like in the screenshot above! Go back to the tokenlist, edit the certificate token und set a PIN again.
After this step you can download the pkcs12 or let the user login via the selfservice portal and download it’s own certificate.
Now you can use it for any kind of certificate based authentication.
Have fun!